WHAT WE DO
Our Mission: Guardians of Digital Childhood
Our commitment is to safeguard children from all forms of sexual abuse by developing an app with AI technology to protect children from online sexual abuse.
We Will Stop Child Abuse
Sexual abuse manifests in various forms, and our mission is to combat all of them effectively.

Sextortion
Sextortion involves using sexual images to coerce victims, often for financial gain. 84% of victims did not seek help because they were too embarrassed or ashamed. Unfortunately, sextortion greatly increases the risk of suicide.
Our system…
… prevents the sending of sexual images, providing crucial protection against exploitation.

CSAM
Child Sexual Abuse Material, including AI-generated content, involves images, videos, or texts depicting child abuse in all conceivable forms.
Our system…
… searches for and blocks the distribution of CSAM, including AI-generated versions, to protect vulnerable individuals.

Sexting & Non-Consensual Intimate Imagery
Children’s constant access to digital devices has heightened sexting and the sharing of non-consensual intimate images.
As the internet never forgets, victims are repeatedly approached about images and videos. They therefore experience the trauma again and again.
Our system…
… takes prompt action by blocking sexting messages as they arrive and intercepting texts from children before they are sent.

Grooming
Grooming involves building a relationship with children to prepare them for abuse by manipulating trust and using fear and shame to maintain silence. Immediate action is vital to protect children from these deceptive practices with lasting psychological impacts.
Our system…
… intervenes upon detecting manipulation, immediately terminating the conversation to prevent further harm.… intervenes upon detecting manipulation, immediately terminating the conversation to prevent further harm.
How it works
Step 1:
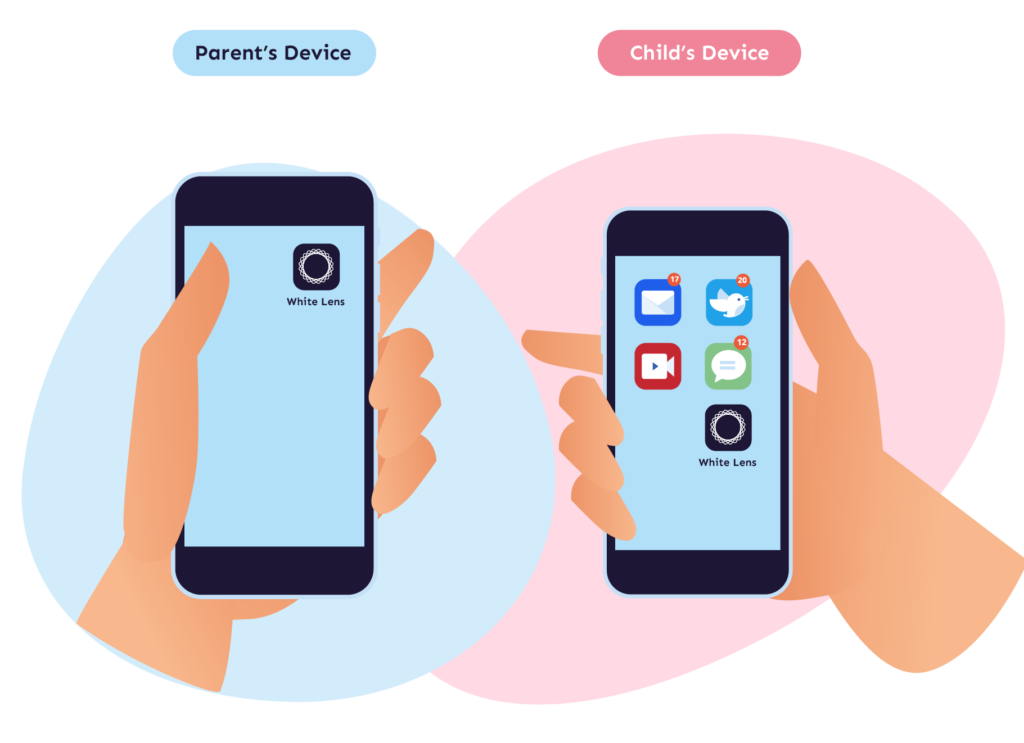
Install our app on both the child’s and the parent’s digital devices, including smartphones, tablets, and laptops. Our app operates discreetly in the background, providing protection without disrupting the device’s functionality.
Step 2:
The app analyzes audio, video, images, and text (both sent and received) for harmful and illegal content, particularly related to sexual abuse and pornography. This proactive analysis happens before the child can see or send the content, as we intercept data before it is encrypted.

Step 3:
It blocks harmful content and notifies the child, explaining why it was blocked.

Step 4:
The app sends alerts to parents about suspicious activity. They receive notifications only for identified threats, respecting your child’s privacy and independence.

Step 5:
Parents can decide what happens to suspicious data (delete or report case). If they choose to report the case, it will be sent to the appropriate authority for further investigation.

There are already many nanny apps
- Complete Surveillance: Full monitoring, compromising children's privacy and causing discomfort.
- Trust Issues: Excessive monitoring damages independence and trust.
- No Privacy by Design: Lack privacy considerations from the start.
- Misuse: Can be used to spy on spouses, linked to domestic violence.
- Delayed Filtering: Can't intercept inappropriate content before it reaches the device.
This is how we do it differently
- Safe Exploration: Real alerts without constant updates, allowing safe, supervised exploration.
- Trust: Builds trust, ensuring children feel protected with minimal restrictions.
- No Stalking: Accesses devices only for external attacks and when children post content themselves.
- Privacy by Design: Emphasizes children's rights and privacy, with data ownership for parents.
- Content Filtering: Real-time analysis to block inappropriate content before viewing.
Privacy by Design: Our Approach

Our app is designed with the 'Privacy by Design' principle at its core, ensuring that data privacy and security are paramount from the very beginning.

Parents have full control over all generated data. Children have the assurance that parents cannot simply read everything. Location tracking is also not feasible.

Parents choose what happens to suspicious data (delete, archive or continue tracking). Only after receiving an alert do they obtain access to the content in question.

Our app operates discreetly in the background, providing robust protection without disrupting the device’s functionality.
Our Milestones to Product Launch

2024
Funding
Right now we are at the funding stage of our project. Securing sufficient resources for the tasks ahead.
2024
Development
Application development starts in Q4|2024 in collaboration with of our partners.
2026
Prototype
A first working version (MVP) of our application is released, planned in 2026.
2027
Product Launch
Official launch of our app across US and European markets is targeted for Q4|2027.